Emerging Technology
Emerging Technology
Supporting Innovation
Continuum works with companies ranging from seed stage startups to the largest technology companies in the world, helping them drive products to successful adoption. By helping them fit their solutions to current market trends and understand their customer’s business challenges, we drive results for them, their customers, and the value-chain that helps drive product to market. Our team is privileged to work with some of the most interesting early-stage technologies, driving the innovation and new methodologies that are leading the next technology evolution.

Supporting Innovation
Continuum works with companies ranging from seed stage startups to the largest technology companies in the world, helping them drive products to successful adoption. By helping them fit their solutions to current market trends and understand their customer’s business challenges, we drive results for them, their customers, and the value-chain that helps drive product to market. Our team is privileged to work with some of the most interesting early-stage technologies, driving the innovation and new methodologies that are leading the next technology evolution.

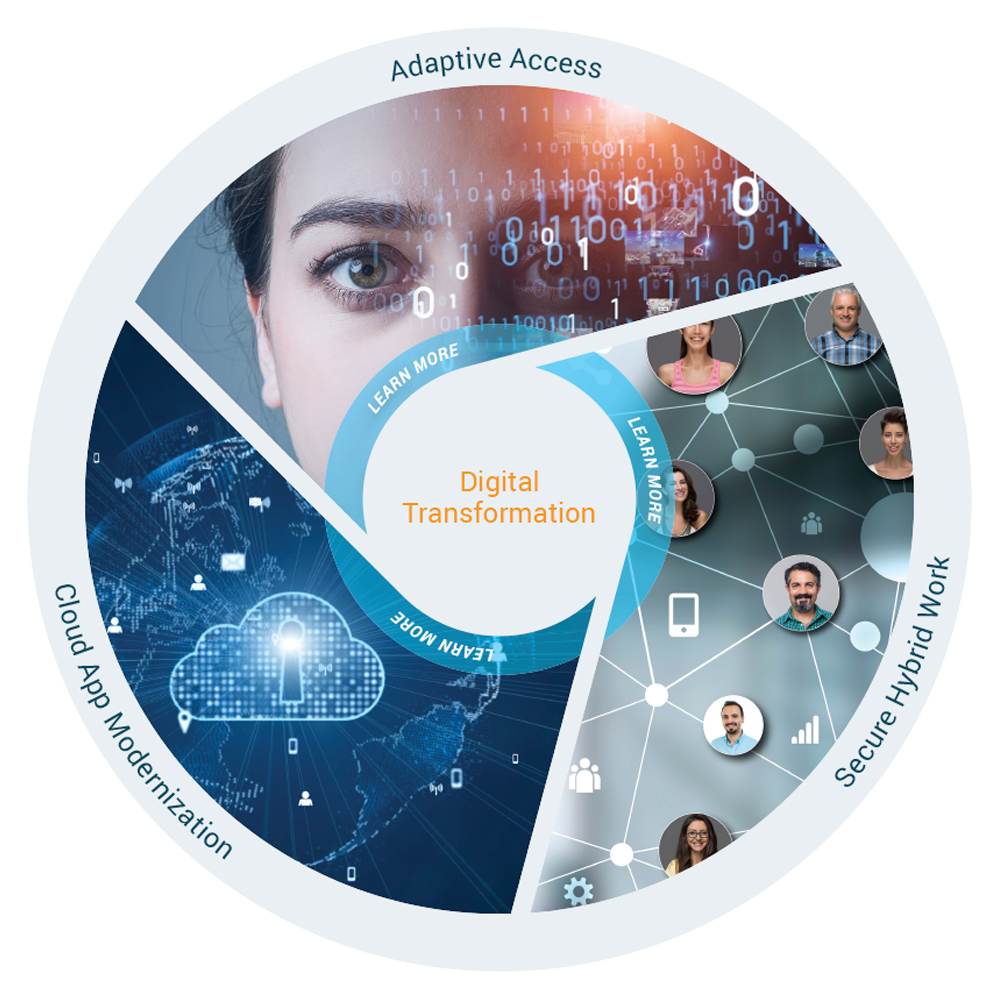
Adaptive Access:
The security landscape is littered with point products solving specific problems and new buzzwords providing old promises without a clear path to execution. What’s needed is a holistic solution to the core problem of providing the right access, to the right actor, at the right time. Learn how emerging tech is addressing this challenge without bolting on another solution or requiring a replacement of existing effort and tooling.

Secure Hybrid Work:
In today’s world, work happens everywhere. This simultaneously expands productivity and strains IT delivery. Providing agile, secure productivity to users wherever they work is no easy task. IT must protect the sensitive data they work with, without burdening users with cumbersome security hassles. Learn how new technologies are driving remote productivity, securely.

Cloud App Modernization:
With technology shifting at an ever-increasing pace, yesterday’s innovative system can quickly become today’s orphaned legacy environment. Having solutions that can bring yesterday’s applications and workloads forward, provisioning and managing them on the private or public environment of your choice is critical to success. Learn how modern solutions are addressing app modernization and cloud migration without leaving legacy behind.
Delivering Pervasive Identity as the Foundation of Trust:
Information security is built upon trust relationships. Trust of users, devices, and things (actors) accessing applications and data (resources). Modern approaches such as ‘Zero Trust’ aren’t used literally, instead they refer to models that eliminate ‘default trust’, trust without verification or enforcement. Identity is a foundational requirement for trust.
Delivering Holistic Lifecycle Management for Kubernetes:
As containerization has become the standard deployment model for cloud applications, Kubernetes has emerged as the dominant leader in container management. This market consolidation has brought significant advantages while leaving one major gap. How do you manage multiple Kubernetes clusters across multiple environments and distributions?
Delivering a Secure Desktop Experience for Hybrid Work:
With hybrid being rapidly normalized and many organizations moving to remote-first or remote-only models, data retention and access is top of mind. Managing desktop images, and security profiles, across remote devices that may never return to a corporate office is no easy task.

Adaptive Access:
The security landscape is littered with point products solving specific problems and new buzzwords providing old promises without a clear path to execution. What’s needed is a holistic solution to the core problem of providing the right access, to the right actor, at the right time. Learn how emerging tech is addressing this challenge without bolting on another solution or requiring a replacement of existing effort and tooling.

Secure Hybrid Work:
In today’s world, work happens everywhere. This simultaneously expands productivity and strains IT delivery. Providing agile, secure productivity to users wherever they work is no easy task. IT must protect the sensitive data they work with, without burdening users with cumbersome security hassles. Learn how new technologies are driving remote productivity, securely.

Cloud App Modernization:
With technology shifting at an ever-increasing pace, yesterday’s innovative system can quickly become today’s orphaned legacy environment. Having solutions that can bring yesterday’s applications and workloads forward, provisioning and managing them on the private or public environment of your choice is critical to success. Learn how modern solutions are addressing app modernization and cloud migration without leaving legacy behind.
Delivering Pervasive Identity as the Foundation of Trust:
Information security is built upon trust relationships. Trust of users, devices, and things (actors) accessing applications and data (resources). Modern approaches such as ‘Zero Trust’ aren’t used literally, instead they refer to models that eliminate ‘default trust’, trust without verification or enforcement. Identity is a foundational requirement for trust.
Delivering Holistic Lifecycle Management for Kubernetes:
As containerization has become the standard deployment model for cloud applications, Kubernetes has emerged as the dominant leader in container management. This market consolidation has brought significant advantages while leaving one major gap. How do you manage multiple Kubernetes clusters across multiple environments and distributions?
Delivering a Secure Desktop Experience for Hybrid Work:
With hybrid being rapidly normalized and many organizations moving to remote-first or remote-only models, data retention and access is top of mind. Managing desktop images, and security profiles, across remote devices that may never return to a corporate office is no easy task.



