Cyber Threat Intelligence (CTI) has become a discipline that is easily misunderstood and incorrectly applied. Leaders in InfoSec may have learned how CTI teams can improve their security posture, but may not know how to effectively use CTI in their core functions.
Some companies use Threat Intelligence teams as a type of news aggregator for cyber-related events, providing the C-Suite with the latest information on “good-to-know” events. Regurgitating the news is not Cyber Threat Intelligence.
This may be why many InfoSec teams are implementing automation for tasks that CTI analysts were previously conducting. If your organization’s CTI team is only doing the minimum or doesn’t know the true value of having a CTI analyst, then it may make sense financially in the near term, until you find a professionally trained and competent CTI analyst. In the long term, organizations need to understand what a real CTI team and their deliverables look like.
As you dive deeper into this article, you’ll gain an understanding of why CTI can be so crucial to an organization’s business operations, including how CTI can be the catalyst for an improved cybersecurity defense posture.
Cyber Threat Intelligence (CTI) has become a discipline that is easily misunderstood and incorrectly applied. Leaders in InfoSec may have learned how CTI teams can improve their security posture, but may not know how to effectively use CTI in their core functions.
CTI can be thought of as an “Ambassador to the Threat for an Organization,” which assists in understanding who the organization is, in relation to its potential threats. CTI is not just a task to be done by Incident Response members who may be looking for the next step in their professional growth. Rather, CTI is an “Art” and “Science” that requires intentional and contextual research, with the endstate of driving operations.
This raises the question: What foundational skills do Cyber Threat Intelligence professionals possess that set them apart from other InfoSec professionals? It comes from the training. The “Art” and “Science” discussed include important research, writing, and critical-thinking skills. Those skills come from well-established practices in understanding subjects and finding relevancy in complex problem sets.
Threat Intelligence and Why Organizations Need It:
Effective threat intelligence turns unknown threats into known challenges, allowing us to stay one step ahead in the ever-evolving landscape of cyber threats. It is our early warning system in the world of cybersecurity, guiding us to anticipate and neutralize threats before they become full-blown crises.
By transforming raw data into actionable insights, organizations can move from a reactive to a proactive stance, ensuring preparedness rather than surprise, by the next cyber threat.
It turns data into knowledge and knowledge into action, empowering organizations to defend their digital landscapes, and mitigate cyber threats. Transforming our approach to cybersecurity ensures that we stay ahead of evolving challenges.
What an organization can expect from a CTI analyst and their deliverables:
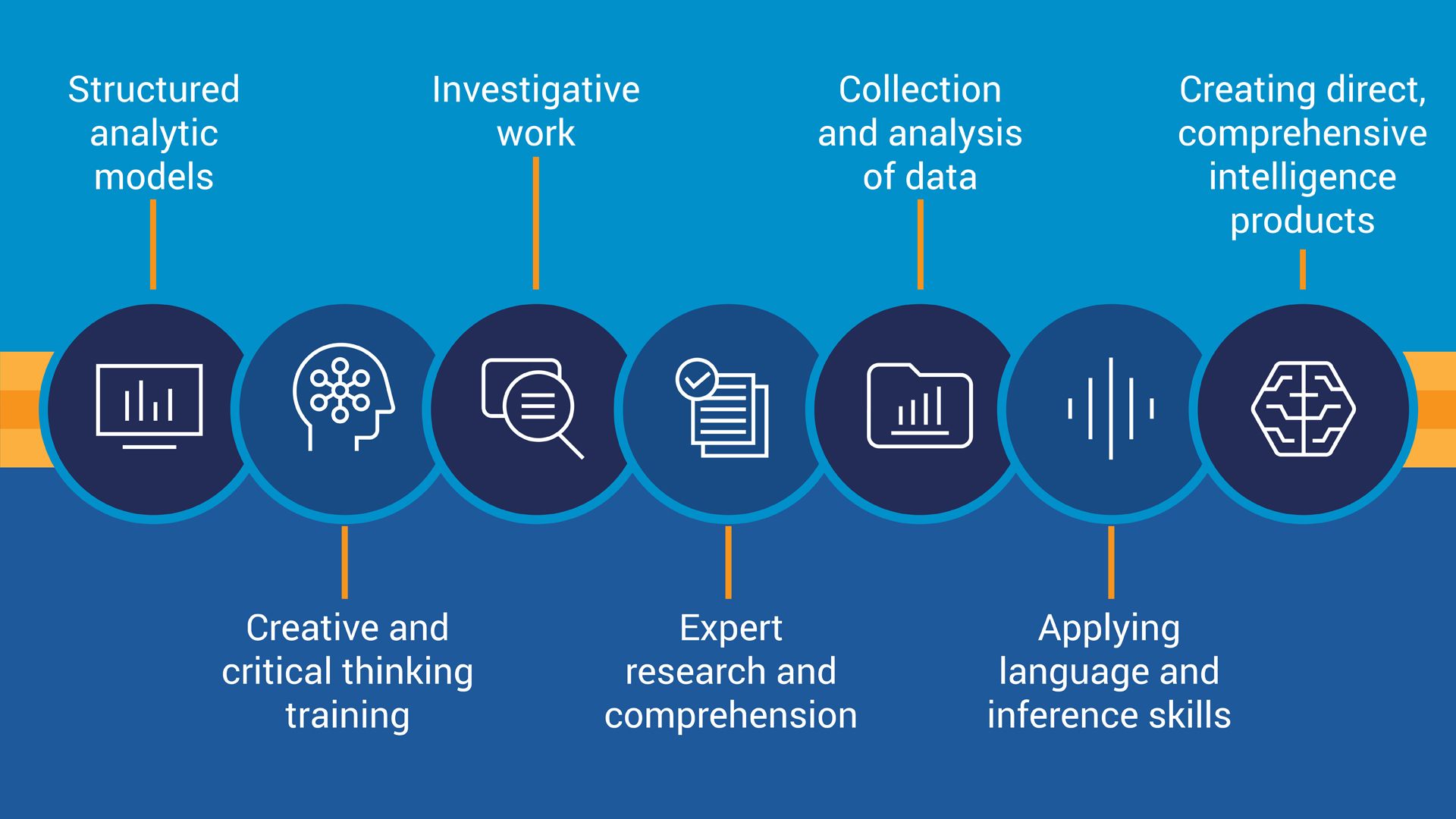
As discussed, Threat Intelligence uses a scientific and artistic approach to this profession. The scientific approach uses analytic knowledge to create models, cognitive processes, scientific reasoning, and investigative work, to collect data and analyze intelligence information. The artistic approach uses holistic knowledge, applying language and deduction skills, research, and creating direct, comprehensive intelligence products; which are used to help:
- Decision-making leaders create strategies through policy and procedures.
- Managerial entities to give technical direction and operational guidance.
- Professional entities use technical application and expertise to reach endstate.
Once the intelligence process is complete, consumers give feedback; the intelligence entity conducts refinement, thus being a dynamic, and developing process.
Threat Intelligence and Decision-Making:
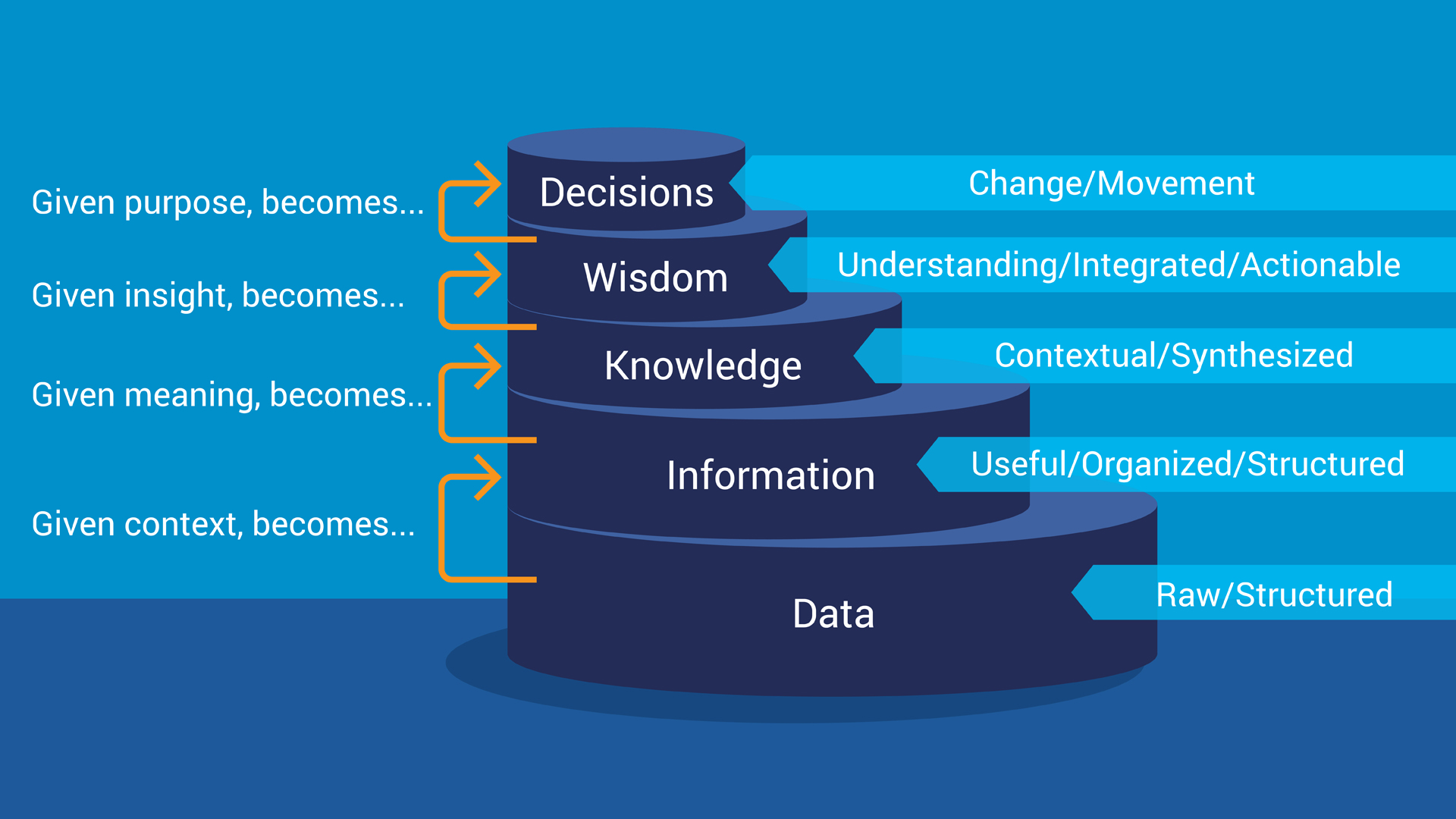
Threat intelligence analysis uses evidence-based knowledge about an existing or emerging threat to assets and people, to create context, indicators, implications, and actionable advice. The end product then is used to inform decisions on response to those threats. To enrich data into intelligence, analysts use a model that is called the Data, Information, Knowledge, Wisdom (DIKW) model. It is a hierarchical model that shows the relationship and transformation from raw data to actionable insights.*
The DIKW model is the critical thinking mechanism behind the Intelligence Cycle, that the Intelligence Community has used for 75+ years**. This is because it follows the inherent process in which humans extract and leverage valuable insights, create awareness, and then problem-solve. It is derived from the profession of data science and analytics.
The Data, Information, Knowledge, Wisdom (DIKW) model:
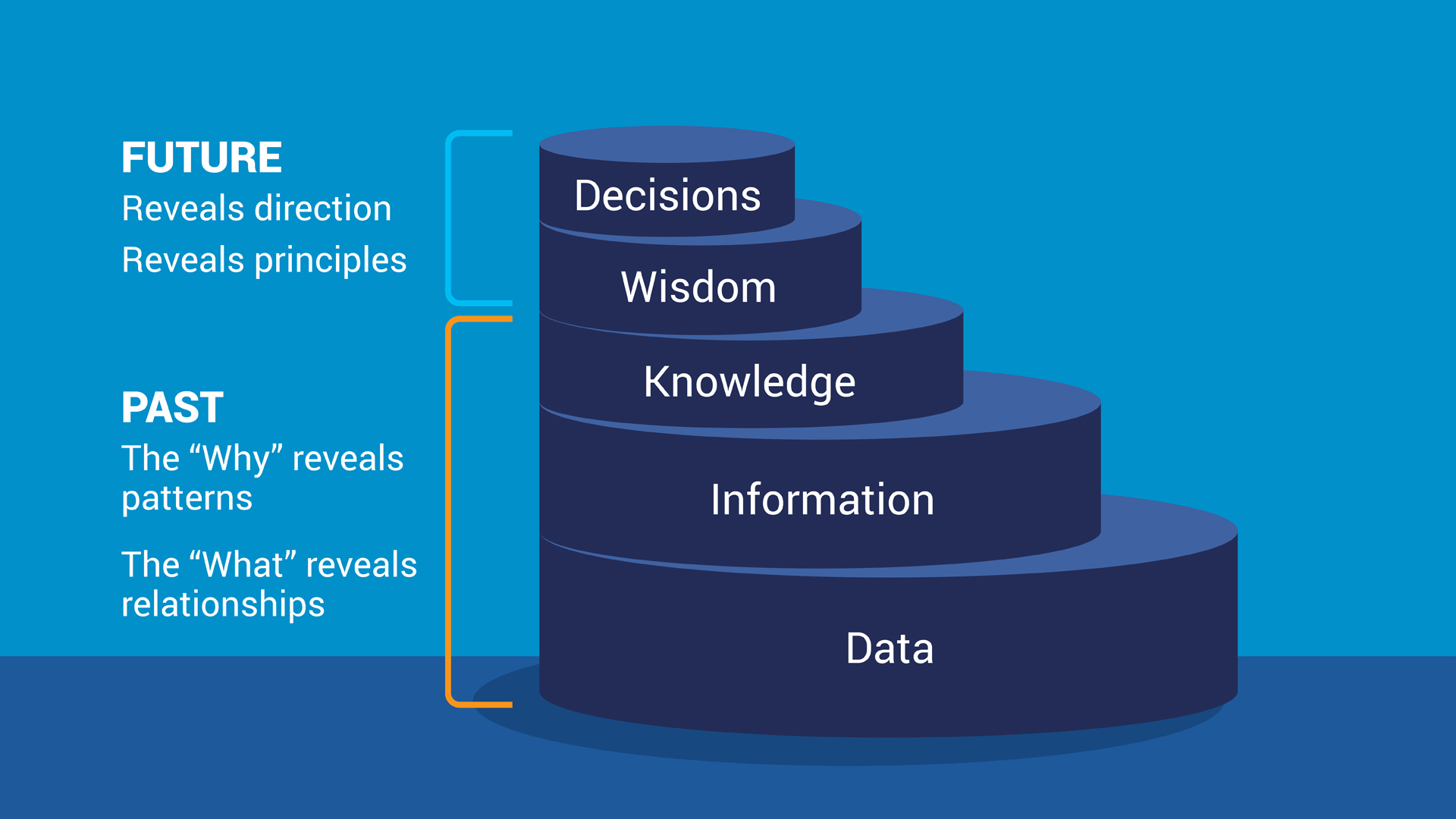
Information science gives us the DIKW model, to look at various ways of extracting insights and value from all sorts of data: big, small, historical, and current. In the model shown here, the Decisions stage is added to the model, as it is the purpose of attaining Wisdom. Just like building a car, it starts as thousands of pieces, and it is built based on relevancy, action, and purpose. You can think of Decisions as deciding on a destination after you assemble the car.
The Intelligence Cycle:
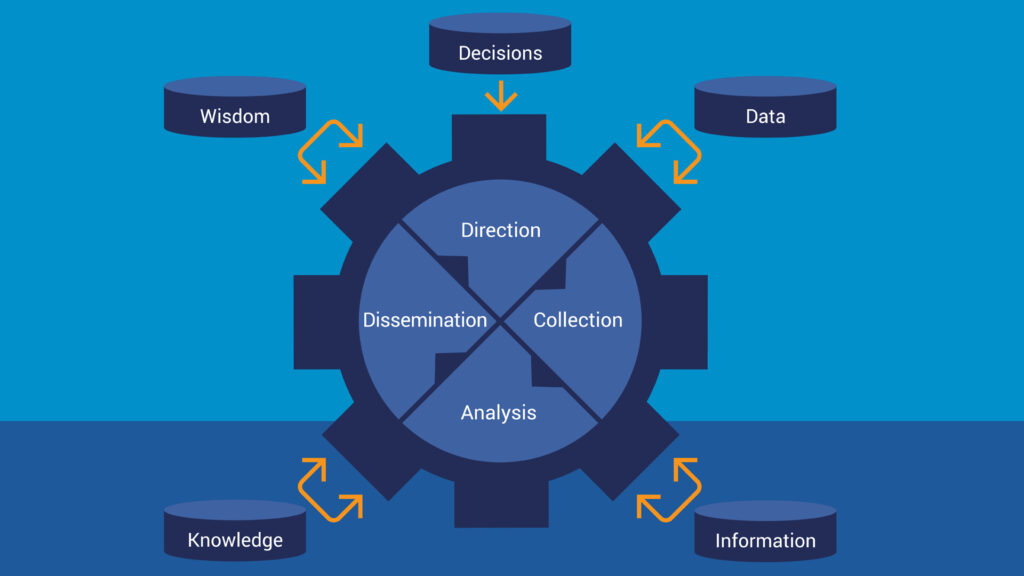
The Intelligence Cycle is the process an intelligence analysis team uses to advise and interpret threats to an organization, for the purpose of following the organization’s mission statement and reaching the desired endstate.
This process goes through 4 stages:
- Direction: Where the decision-makers provide their desired goals (intelligence directives), create requirements on information, request for advisement on threat activity against the organization, and provide their endstate.
- Collection: Once requirements and priorities have been established, data is collected, for the purpose of creating intelligence information. Internal collection of data is often unrefined and needs context to become intelligence information. External collection of data is often refined, but needs further context, and applied appropriately to an organization’s internal data, to become intelligence information.
- Analysis: The processing and exploitation of intelligence information, which is interpreted, evaluated, and integrated, from all applicable data, and becomes intelligence.
- Dissemination: The creation of an intelligence product, distributes the intelligence from the producer to the consumer. This is where the intelligence is standardized for consumption, to the benefit of the consumer. The consumer takes the intelligence information and applies it to their tasks, procedures, or policies, in the best manner to reach the organization’s desired endstate.
The “So What?” & Why Every Organization Should Care:
Cyber Threat Intelligence (CTI) is a pivotal discipline in cybersecurity, often misunderstood and underutilized despite its critical role. While some organizations treat CTI as mere news aggregation, true CTI integrates art and science through deliberate research and contextual analysis. CTI professionals, trained rigorously in research, critical thinking, and contextual analysis, excel in transforming raw data into actionable insights.
Guided by frameworks like the DIKW model and the Intelligence Cycle, CTI significantly enhances organizational resilience. By delivering evidence-based insights and contextualizing threats, CTI empowers decision-makers to formulate informed strategies, steer technical direction, and optimize operational procedures. The continuous feedback loop inherent in the Intelligence Cycle ensures that CTI remains adaptive and effective, mitigating biases and addressing informational gaps.
Recognizing CTI’s potential goes beyond reactive measures, positioning it as a proactive force in defending against evolving cyber threats and driving strategic initiatives. Organizations that embrace CTI unlock its capacity to safeguard their digital assets and uphold robust cybersecurity postures in an increasingly complex threat landscape.
If you want to learn more about deeply technical concepts like this, business-relevant GTM strategies, marketing insights, and other trending stories, make sure you’re following Transformation Continuum on LinkedIn so you never miss a beat!

There's more to discover!
You can gain access to more helpful resources just like this by subscribing to our Linkedin Newsletter, “Continuum at The Edge”. Our monthly newsletter provides the latest digital transformation news, noteworthy content, and events happening at the edge of tech. By joining our subscriber community, not only will you unlock additional articles, but you have the ability to join in on insightful and eye-opening conversations with our audience.

There's more to discover!
You can gain access to more helpful resources just like this by subscribing to our Linkedin Newsletter, “Continuum at The Edge”. Our monthly newsletter provides the latest digital transformation news, noteworthy content, and events happening at the edge of tech. By joining our subscriber community, not only will you unlock additional articles, but you have the ability to join in on insightful and eye-opening conversations with our audience.

